Cybersecurity isn’t just about firewalls and antivirus software – sometimes, the biggest risk is people. That’s where social engineering comes in. It’s sneaky, it’s clever, and it’s catching out businesses of all sizes every day.
So, how to prevent social engineering attacks is the real question. In this guide, we’ll break down what social engineering is, the types of attacks you should look out for, real-life examples, and how to prevent social engineering attacks in simple, practical ways – without the jargon.
What is social engineering and how does it work?
Social engineering is when cybercriminals trick someone into doing something they shouldn’t – like handing over passwords, clicking dodgy links, or letting someone into the building without checking who they are.
Unlike technical hacks, social engineering relies on human psychology – things like trust, curiosity, fear, or a desire to be helpful. Attackers use this to get past your defences.
They often follow a pattern:
- Research the target
- Build trust
- Exploit that trust
- Access data or systems
It could be a phishing email, a fake phone call from “IT”, or even someone tailgating into your office. It’s simple, but dangerous.
If you think your business has been targeted, report it through Action Fraud, the UK’s national cybercrime reporting centre.
Types of social engineering attacks
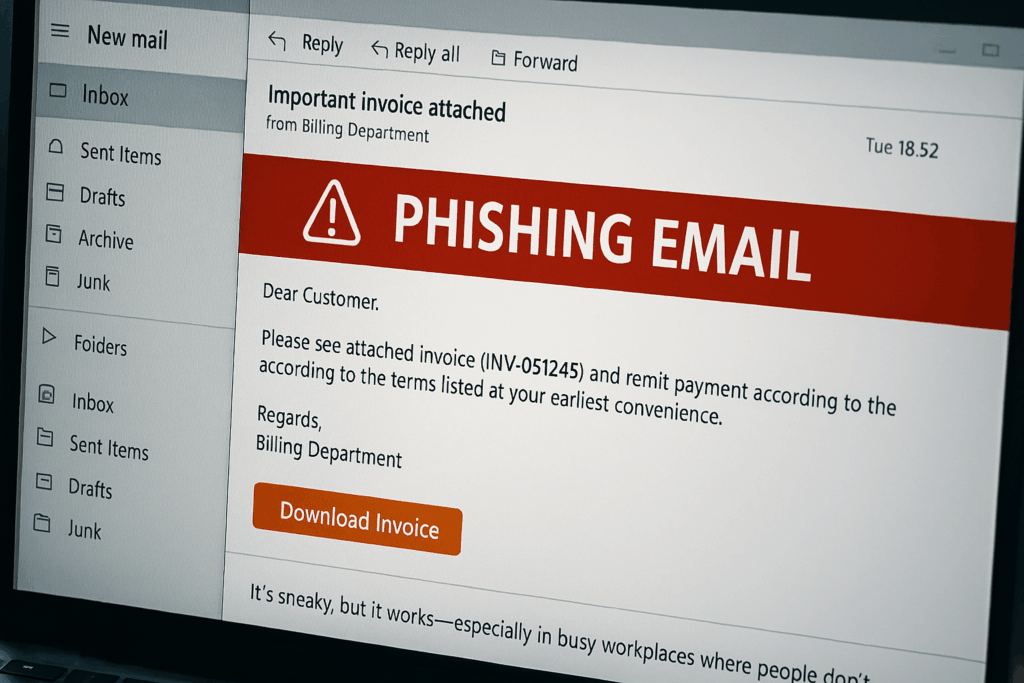
Emails
Phishing emails are the most common. They might:
- Look like they’re from your bank or IT team
- Urge you to reset your password
- Ask you to click a suspicious link or download a file
Spear phishing is more targeted. These emails look even more convincing because attackers do their homework—like pretending to be your manager or referencing a recent project.
Phone
Known as vishing, this involves fake calls from “tech support”, HMRC, or even your CEO. Some use AI-generated voices to sound like someone you know.
Online
Hackers embed malware in websites or ads. Even sites you trust can get compromised. One click and your system could be infected.
Tailgating
This happens when someone physically follows an authorised person into a secure area—like an office or server room. They might pretend to be a delivery person or forget their access card. Read more about tailgating here.
Real-Life examples of social engineering attacks
WHO Phishing Scam
During COVID-19, scammers sent fake emails claiming to be from the World Health Organization. These emails contained malware and led to 450 compromised accounts.
Red Kite Community Housing
A housing charity lost £932,000 after attackers created a fake supplier website and email trail. The charity thought they were paying a genuine invoice—but it went straight to the criminals.
10 practical tips on how to prevent social engineering attacks
You don’t need to be a tech expert to stay safe—you just need to stay sharp. Here’s what works:
1. Train Your Team
Most attacks work because someone didn’t know better. Run regular training sessions on:
- Spotting phishing emails
- Saying no to suspicious calls
- Reporting anything odd—even if it feels minor
At IT Backbone, we offer tailored cybersecurity awareness training to help your team stay alert.
2. Use Multi-Factor Authentication (MFA)
Even if someone gets your password, MFA adds a second layer of defence—like a code sent to your phone. It’s one of the easiest and most effective ways to block attackers.
3. Improve Email Security
Use tools like Mimecast or Microsoft Defender to catch phishing emails before they hit your inbox.
4. Detect Tailgating
Use CCTV, badge access logs, or even AI-powered cameras to track who’s entering your building—and when. Encourage staff to speak up when something feels off.
5. Limit Access
Don’t give everyone access to everything. Restricting access is another example of how to prevent social engineering attacks, since it reduces the impact if credentials are compromised. Even if someone slips through, the damage is limited.
6. Keep Software Updated
Old software often has known vulnerabilities. Update regularly to close those gaps—and enable auto-updates where possible.
7. Think Before You Click
If something feels rushed, suspicious, or too good to be true—it probably is. Pause, think, and verify before taking action.
FAQs about how to prevent social engineering attacks
What’s the most common social engineering attack?
Phishing emails are the most common. They pretend to be from trusted sources to trick you into sharing sensitive data.
How can I tell if an email is fake?
Look for:
- Poor spelling or grammar
- Suspicious links (hover to preview)
- Urgent or threatening language
- Unfamiliar email addresses
Can antivirus software stop social engineering?
Not always. Antivirus helps, but it doesn’t teach users how to prevent social engineering attacks. That comes from awareness, training, and strong processes.
How do I protect my business from tailgating?
Install badge-controlled access, train your team, use surveillance, and foster a “no tailgating” culture.
FAQs about IT Backbone
Who is IT Backbone?
We’re a UK-based IT support and cybersecurity provider helping businesses stay safe—whether you’re remote, hybrid, or office-based.
What services do you offer?
- Managed IT support
- Cybersecurity training and strategy
- Cloud solutions
- Tailgating and Zero Trust assessments
Can you help prevent social engineering attacks?
Absolutely. We offer training, penetration testing, Zero Trust strategies, and real-time threat monitoring to keep your business secure.
Ready to Stop Social Engineering Before It Starts?
At IT Backbone, we believe prevention is better than cure—which is why we show organisations exactly how to prevent social engineering attacks with training, audits, and security strategies.
Let’s chat about making your business safer today.

